Secure Raspberry Pi: Free RemoteIoT SSH Key Setup [Guide]
Are you tired of complex and costly solutions for managing your Raspberry Pi remotely? Embrace the power of seamless and secure remote management with the Remote IoT platform's SSH key feature, offered completely free of charge! This game-changing capability democratizes remote access, leveling the playing field for users of all budget sizes.If you've been on the hunt for a robust yet accessible platform that enables secure remote control of your Raspberry Pi using SSH keys, then this is precisely the resource you've been waiting for. We'll guide you through the process of harnessing the potential of Remote IoT, demonstrating how it can transform your Raspberry Pi experience.
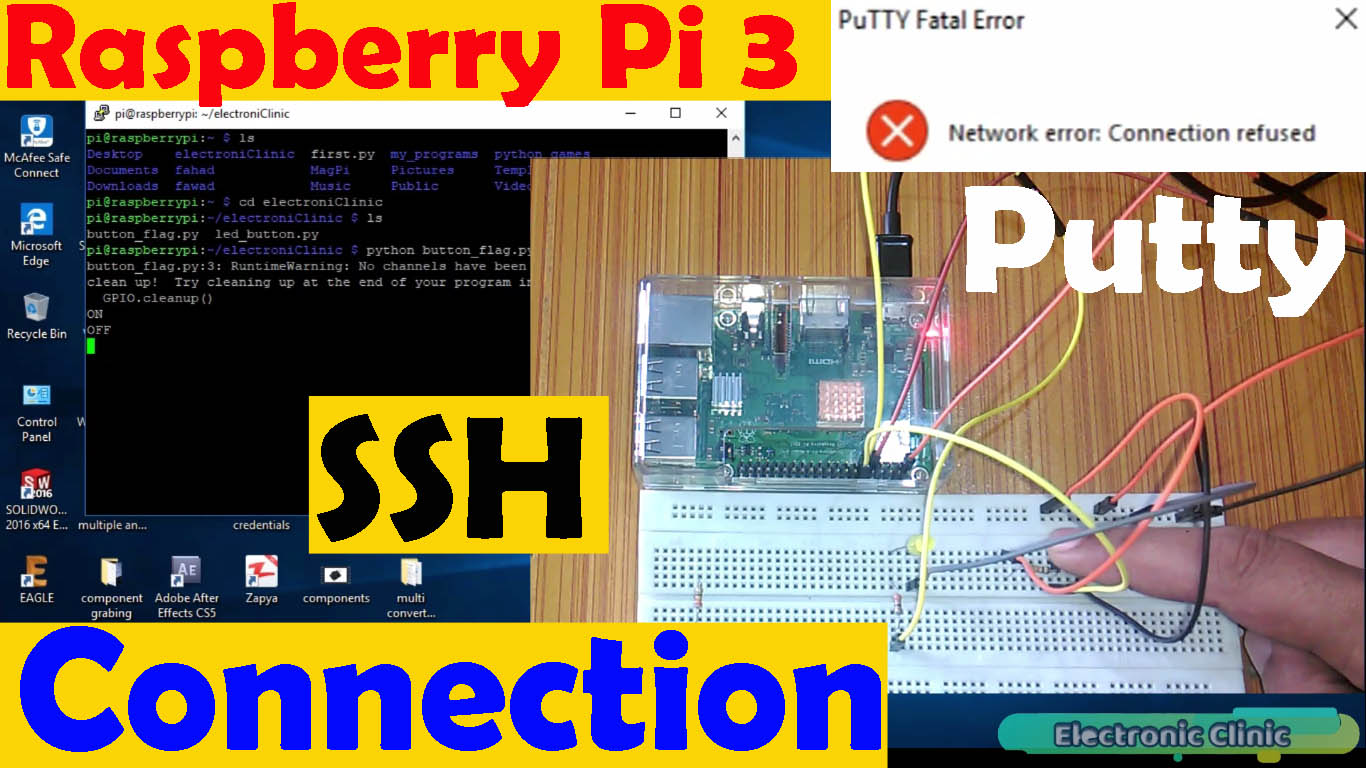
The integration of a free Remote IoT platform with SSH key authentication for Raspberry Pi represents a significant leap forward in enabling secure and streamlined remote access to these versatile devices. It's engineered to make the entire experience intuitive and efficient.Setting up SSH keys on your Raspberry Pi via the Remote IoT platform is designed to be a simple process, achievable in just a few steps. We'll walk you through each stage, ensuring a smooth and successful setup.Establishing a free Remote IoT platform with SSH keys for your Raspberry Pi is a surprisingly straightforward endeavor. The key is to follow a series of carefully orchestrated steps.By adhering to these essential steps, you can guarantee a secure and efficient connection between your Raspberry Pi and the Remote IoT platform. This unlocks a vast realm of possibilities for remote access and control, expanding the horizons of your IoT projects.Once you've successfully created your account on the Remote IoT platform, the next crucial step is to connect your Raspberry Pi. This connection is established by following the detailed instructions provided by the platform.Typically, connecting your Raspberry Pi involves the installation of a lightweight agent. This agent acts as the bridge between your device and the Remote IoT platform, facilitating communication and control.The next critical phase is the generation and configuration of SSH keys. These keys are the cornerstone of secure remote access, providing a robust alternative to traditional password-based authentication.With your Raspberry Pi seamlessly connected to the Remote IoT platform, the platform will automatically generate and configure SSH keys, ensuring a secure and protected connection for all subsequent remote access.The inherent compatibility of the Raspberry Pi with the Remote IoT platform significantly amplifies its appeal. It's a top choice for both IoT enthusiasts and seasoned professionals seeking a reliable and versatile solution.To further enrich your understanding of free Remote IoT platforms, SSH keys, and the intricacies of Raspberry Pi integration, we encourage you to explore the wealth of available resources. These resources offer in-depth knowledge and practical insights.A critical aspect of securing your Raspberry Pi is the proper configuration of SSH. This configuration is essential for establishing secure remote connections.Now that you've chosen a Remote IoT platform, it's time to delve into the configuration of SSH on your Raspberry Pi. This is where you'll fine-tune the settings to optimize security and performance.This section will serve as your comprehensive guide, leading you through the process of setting up SSH keys, configuring the SSH server, and establishing a remote connection to your Raspberry Pi. We'll break down each step into manageable components.SSH keys provide a significantly more secure method of authentication compared to traditional passwords. They are less susceptible to brute-force attacks and offer a higher level of protection.If you're reading this, the chances are high that you're actively searching for a dependable and free Remote IoT platform that seamlessly supports SSH key management for your Raspberry Pi devices. You're seeking a solution that balances security, functionality, and cost-effectiveness.Well, rest assured, you've arrived at the ideal destination! We're dedicated to providing you with the knowledge and resources you need to make informed decisions and implement secure remote management strategies.Are you specifically seeking the best Remote IoT platform that offers free SSH key authentication on your Raspberry Pi? Do you prioritize security and ease of use?You're unequivocally in the right place! We'll help you navigate the landscape of available platforms and identify the one that best aligns with your specific needs and requirements.By proactively addressing these common challenges, you can ensure a seamless and successful integration of your Raspberry Pi with a Remote IoT platform. This will pave the way for a productive and secure remote management experience.Why should you even consider using a Remote IoT platform with SSH keys in the first place? What are the compelling reasons that make this approach so attractive?Using a Remote IoT platform with SSH keys provides a plethora of advantages, ranging from enhanced security to simplified device management. It's a win-win scenario for anyone managing Raspberry Pi devices remotely.Let's delve deeper into the reasons why SSH keys are superior to passwords. Passwords, while ubiquitous, are inherently vulnerable. They can be cracked through brute-force attacks, phishing scams, or simply by guessing. SSH keys, on the other hand, rely on cryptographic principles, making them significantly more resistant to such attacks.Moreover, SSH keys eliminate the need to memorize complex passwords. You simply store the private key securely on your local machine, and the public key is placed on the Raspberry Pi. This eliminates the risk of forgetting passwords or having them stolen.The streamlined device management capabilities of a Remote IoT platform are also a major draw. These platforms provide a centralized interface for managing multiple Raspberry Pi devices, simplifying tasks such as software updates, configuration changes, and monitoring.With a Remote IoT platform, you can remotely access and control your Raspberry Pi from anywhere in the world, as long as you have an internet connection. This opens up a world of possibilities for remote monitoring, data collection, and automation.Imagine, for instance, that you're running a weather station on your Raspberry Pi. With a Remote IoT platform, you can remotely monitor the sensor data, adjust the settings, and even restart the device if necessary, all from the comfort of your home or office.Or perhaps you're using your Raspberry Pi to control a robotic arm. With a Remote IoT platform, you can remotely program and control the arm, even if you're thousands of miles away.The possibilities are virtually limitless. A Remote IoT platform empowers you to harness the full potential of your Raspberry Pi, regardless of your location.But how do you choose the right Remote IoT platform? There are many options available, each with its own set of features and pricing plans.The first step is to identify your specific needs and requirements. What are you planning to use your Raspberry Pi for? What features are most important to you? What is your budget?Once you have a clear understanding of your needs, you can start comparing different Remote IoT platforms. Look for platforms that offer SSH key authentication, a user-friendly interface, and comprehensive device management capabilities.Also, consider the platform's security features, its scalability, and its level of support. You want to choose a platform that is reliable, secure, and capable of growing with your needs.Don't be afraid to try out a few different platforms before making a decision. Many platforms offer free trials or free tiers, allowing you to test their features and see if they meet your requirements.Once you've chosen a Remote IoT platform, the next step is to set up SSH keys on your Raspberry Pi. This is a relatively straightforward process, but it's important to follow the instructions carefully.The first step is to generate an SSH key pair on your local machine. This key pair consists of a private key and a public key. The private key should be kept secret, while the public key can be shared with the Raspberry Pi.You can generate an SSH key pair using a variety of tools, such as ssh-keygen on Linux or macOS, or PuTTYgen on Windows.Once you've generated the key pair, you need to copy the public key to the Raspberry Pi. This can be done using the ssh-copy-id command, or by manually copying the key to the ~/.ssh/authorized_keys file.After the public key is copied to the Raspberry Pi, you can disable password-based authentication. This will prevent anyone from logging in to your Raspberry Pi using a password, making it much more secure.To disable password-based authentication, you need to edit the /etc/ssh/sshd_config file and set the PasswordAuthentication option to no.Once you've disabled password-based authentication, you can test the SSH key authentication by trying to log in to your Raspberry Pi using your SSH client.If everything is configured correctly, you should be able to log in without being prompted for a password.With SSH key authentication enabled, your Raspberry Pi is now much more secure. You can now access and manage your device remotely with confidence, knowing that your connection is protected by strong cryptographic security.In addition to SSH key authentication, there are several other steps you can take to further secure your Raspberry Pi.For example, you can change the default SSH port from 22 to a higher, less common port. This will make it more difficult for attackers to find your SSH server.You can also use a firewall to restrict access to your Raspberry Pi. A firewall allows you to specify which IP addresses and ports are allowed to connect to your device.Another important security measure is to keep your Raspberry Pi's software up to date. Software updates often include security patches that fix vulnerabilities that could be exploited by attackers.By taking these steps, you can significantly reduce the risk of your Raspberry Pi being compromised.Finally, let's address some common issues that you might encounter when integrating your Raspberry Pi with a Remote IoT platform.One common issue is network connectivity. If your Raspberry Pi is not connected to the internet, you won't be able to access it remotely.Make sure that your Raspberry Pi is connected to a network and that it has a valid IP address. You can check the network connection using the ifconfig command.Another common issue is firewall configuration. If your firewall is blocking SSH traffic, you won't be able to connect to your Raspberry Pi.Make sure that your firewall is configured to allow SSH traffic on the port that you're using.Also, make sure that your SSH keys are properly configured. If the public key is not correctly placed on the Raspberry Pi, you won't be able to log in.Double-check the steps for generating and copying the SSH keys to ensure that everything is set up correctly.If you're still having trouble, consult the documentation for your Remote IoT platform or seek help from the online community. There are many resources available to help you troubleshoot common issues.By addressing these common issues, you can ensure a smooth and successful integration of your Raspberry Pi with a Remote IoT platform. This will allow you to take full advantage of the benefits of remote management and security.


| Feature | Description |
|---|---|
| Platform | Remote IoT Platform |
| Key Feature | SSH Key Authentication (Free) |
| Device | Raspberry Pi |
| Benefit | Secure and Efficient Remote Access |
| Setup Complexity | Straightforward |
| Target User | IoT Enthusiasts, Professionals, Hobbyists |
| Additional Resources | Raspberry Pi Documentation |
The integration of a free Remote IoT platform with SSH key authentication for Raspberry Pi represents a significant leap forward in enabling secure and streamlined remote access to these versatile devices. It's engineered to make the entire experience intuitive and efficient.Setting up SSH keys on your Raspberry Pi via the Remote IoT platform is designed to be a simple process, achievable in just a few steps. We'll walk you through each stage, ensuring a smooth and successful setup.Establishing a free Remote IoT platform with SSH keys for your Raspberry Pi is a surprisingly straightforward endeavor. The key is to follow a series of carefully orchestrated steps.By adhering to these essential steps, you can guarantee a secure and efficient connection between your Raspberry Pi and the Remote IoT platform. This unlocks a vast realm of possibilities for remote access and control, expanding the horizons of your IoT projects.Once you've successfully created your account on the Remote IoT platform, the next crucial step is to connect your Raspberry Pi. This connection is established by following the detailed instructions provided by the platform.Typically, connecting your Raspberry Pi involves the installation of a lightweight agent. This agent acts as the bridge between your device and the Remote IoT platform, facilitating communication and control.The next critical phase is the generation and configuration of SSH keys. These keys are the cornerstone of secure remote access, providing a robust alternative to traditional password-based authentication.With your Raspberry Pi seamlessly connected to the Remote IoT platform, the platform will automatically generate and configure SSH keys, ensuring a secure and protected connection for all subsequent remote access.The inherent compatibility of the Raspberry Pi with the Remote IoT platform significantly amplifies its appeal. It's a top choice for both IoT enthusiasts and seasoned professionals seeking a reliable and versatile solution.To further enrich your understanding of free Remote IoT platforms, SSH keys, and the intricacies of Raspberry Pi integration, we encourage you to explore the wealth of available resources. These resources offer in-depth knowledge and practical insights.A critical aspect of securing your Raspberry Pi is the proper configuration of SSH. This configuration is essential for establishing secure remote connections.Now that you've chosen a Remote IoT platform, it's time to delve into the configuration of SSH on your Raspberry Pi. This is where you'll fine-tune the settings to optimize security and performance.This section will serve as your comprehensive guide, leading you through the process of setting up SSH keys, configuring the SSH server, and establishing a remote connection to your Raspberry Pi. We'll break down each step into manageable components.SSH keys provide a significantly more secure method of authentication compared to traditional passwords. They are less susceptible to brute-force attacks and offer a higher level of protection.If you're reading this, the chances are high that you're actively searching for a dependable and free Remote IoT platform that seamlessly supports SSH key management for your Raspberry Pi devices. You're seeking a solution that balances security, functionality, and cost-effectiveness.Well, rest assured, you've arrived at the ideal destination! We're dedicated to providing you with the knowledge and resources you need to make informed decisions and implement secure remote management strategies.Are you specifically seeking the best Remote IoT platform that offers free SSH key authentication on your Raspberry Pi? Do you prioritize security and ease of use?You're unequivocally in the right place! We'll help you navigate the landscape of available platforms and identify the one that best aligns with your specific needs and requirements.By proactively addressing these common challenges, you can ensure a seamless and successful integration of your Raspberry Pi with a Remote IoT platform. This will pave the way for a productive and secure remote management experience.Why should you even consider using a Remote IoT platform with SSH keys in the first place? What are the compelling reasons that make this approach so attractive?Using a Remote IoT platform with SSH keys provides a plethora of advantages, ranging from enhanced security to simplified device management. It's a win-win scenario for anyone managing Raspberry Pi devices remotely.Let's delve deeper into the reasons why SSH keys are superior to passwords. Passwords, while ubiquitous, are inherently vulnerable. They can be cracked through brute-force attacks, phishing scams, or simply by guessing. SSH keys, on the other hand, rely on cryptographic principles, making them significantly more resistant to such attacks.Moreover, SSH keys eliminate the need to memorize complex passwords. You simply store the private key securely on your local machine, and the public key is placed on the Raspberry Pi. This eliminates the risk of forgetting passwords or having them stolen.The streamlined device management capabilities of a Remote IoT platform are also a major draw. These platforms provide a centralized interface for managing multiple Raspberry Pi devices, simplifying tasks such as software updates, configuration changes, and monitoring.With a Remote IoT platform, you can remotely access and control your Raspberry Pi from anywhere in the world, as long as you have an internet connection. This opens up a world of possibilities for remote monitoring, data collection, and automation.Imagine, for instance, that you're running a weather station on your Raspberry Pi. With a Remote IoT platform, you can remotely monitor the sensor data, adjust the settings, and even restart the device if necessary, all from the comfort of your home or office.Or perhaps you're using your Raspberry Pi to control a robotic arm. With a Remote IoT platform, you can remotely program and control the arm, even if you're thousands of miles away.The possibilities are virtually limitless. A Remote IoT platform empowers you to harness the full potential of your Raspberry Pi, regardless of your location.But how do you choose the right Remote IoT platform? There are many options available, each with its own set of features and pricing plans.The first step is to identify your specific needs and requirements. What are you planning to use your Raspberry Pi for? What features are most important to you? What is your budget?Once you have a clear understanding of your needs, you can start comparing different Remote IoT platforms. Look for platforms that offer SSH key authentication, a user-friendly interface, and comprehensive device management capabilities.Also, consider the platform's security features, its scalability, and its level of support. You want to choose a platform that is reliable, secure, and capable of growing with your needs.Don't be afraid to try out a few different platforms before making a decision. Many platforms offer free trials or free tiers, allowing you to test their features and see if they meet your requirements.Once you've chosen a Remote IoT platform, the next step is to set up SSH keys on your Raspberry Pi. This is a relatively straightforward process, but it's important to follow the instructions carefully.The first step is to generate an SSH key pair on your local machine. This key pair consists of a private key and a public key. The private key should be kept secret, while the public key can be shared with the Raspberry Pi.You can generate an SSH key pair using a variety of tools, such as ssh-keygen on Linux or macOS, or PuTTYgen on Windows.Once you've generated the key pair, you need to copy the public key to the Raspberry Pi. This can be done using the ssh-copy-id command, or by manually copying the key to the ~/.ssh/authorized_keys file.After the public key is copied to the Raspberry Pi, you can disable password-based authentication. This will prevent anyone from logging in to your Raspberry Pi using a password, making it much more secure.To disable password-based authentication, you need to edit the /etc/ssh/sshd_config file and set the PasswordAuthentication option to no.Once you've disabled password-based authentication, you can test the SSH key authentication by trying to log in to your Raspberry Pi using your SSH client.If everything is configured correctly, you should be able to log in without being prompted for a password.With SSH key authentication enabled, your Raspberry Pi is now much more secure. You can now access and manage your device remotely with confidence, knowing that your connection is protected by strong cryptographic security.In addition to SSH key authentication, there are several other steps you can take to further secure your Raspberry Pi.For example, you can change the default SSH port from 22 to a higher, less common port. This will make it more difficult for attackers to find your SSH server.You can also use a firewall to restrict access to your Raspberry Pi. A firewall allows you to specify which IP addresses and ports are allowed to connect to your device.Another important security measure is to keep your Raspberry Pi's software up to date. Software updates often include security patches that fix vulnerabilities that could be exploited by attackers.By taking these steps, you can significantly reduce the risk of your Raspberry Pi being compromised.Finally, let's address some common issues that you might encounter when integrating your Raspberry Pi with a Remote IoT platform.One common issue is network connectivity. If your Raspberry Pi is not connected to the internet, you won't be able to access it remotely.Make sure that your Raspberry Pi is connected to a network and that it has a valid IP address. You can check the network connection using the ifconfig command.Another common issue is firewall configuration. If your firewall is blocking SSH traffic, you won't be able to connect to your Raspberry Pi.Make sure that your firewall is configured to allow SSH traffic on the port that you're using.Also, make sure that your SSH keys are properly configured. If the public key is not correctly placed on the Raspberry Pi, you won't be able to log in.Double-check the steps for generating and copying the SSH keys to ensure that everything is set up correctly.If you're still having trouble, consult the documentation for your Remote IoT platform or seek help from the online community. There are many resources available to help you troubleshoot common issues.By addressing these common issues, you can ensure a smooth and successful integration of your Raspberry Pi with a Remote IoT platform. This will allow you to take full advantage of the benefits of remote management and security.

Unlock The Power Of Free RemoteIoT Platform SSH Key Raspberry Pi For
RemoteIoT Platform SSH Key Free Access For Raspberry Pi The Ultimate Guide

Remote IoT Platform SSH Raspberry Pi Download Free A Comprehensive Guide