IoT Security Guide: Secure Remote Devices With P2P SSH On Ubuntu!
Are your IoT devices leaving your network vulnerable? Securing remote IoT devices through P2P SSH on Ubuntu is not just a best practice; it's a necessity in today's interconnected world, offering a fortified defense against evolving cyber threats. As the Internet of Things (IoT) continues its relentless expansion, the challenges associated with maintaining secure connections become increasingly pronounced for businesses and individuals alike.
The ability to connect remote IoT devices through P2P SSH on Ubuntu is now an indispensable skill for modern developers and system administrators. This article transcends the typical tech tutorial, offering valuable insights whether you're a seasoned professional or a newcomer navigating the complexities of networking. Securely connecting remote IoT devices is a cornerstone of contemporary network management. The surge in IoT technology adoption by both businesses and individuals underscores the paramount importance of ensuring the security of these devices. The discourse surrounding securely connecting remote IoT devices using P2P SSH on Ubuntu emphasizes the critical nature of security protocols.
| Topic | Details |
|---|---|
| Subject | Securing Remote IoT Devices using P2P SSH on Ubuntu |
| Core Concept | Implementing secure peer-to-peer connections for IoT devices via SSH on Ubuntu to enhance network security and streamline device management. |
| Key Benefits |
|
| Technical Aspects |
|
| Target Audience | Developers, system administrators, IT professionals, and tech enthusiasts involved in IoT deployments. |
| Real-world Application | Configuring weather stations to establish secure SSH tunnels to a central Ubuntu server, ensuring data is encrypted and protected from interception. |
| Essential Skills | Knowledge of SSH, Ubuntu server management, network security, and IoT device configuration. |
| Key Takeaway | Mastering secure P2P SSH connections on Ubuntu is crucial for building resilient, safe, and manageable IoT ecosystems, protecting sensitive data and mitigating cyber threats. |
| Further Resources | Ubuntu SSH Server Configuration Tutorial |
- Hyungry Temporary Replacement 2 What Fans Are Saying More
- Lara Rose From Tiktok Star To Millionaire Model More
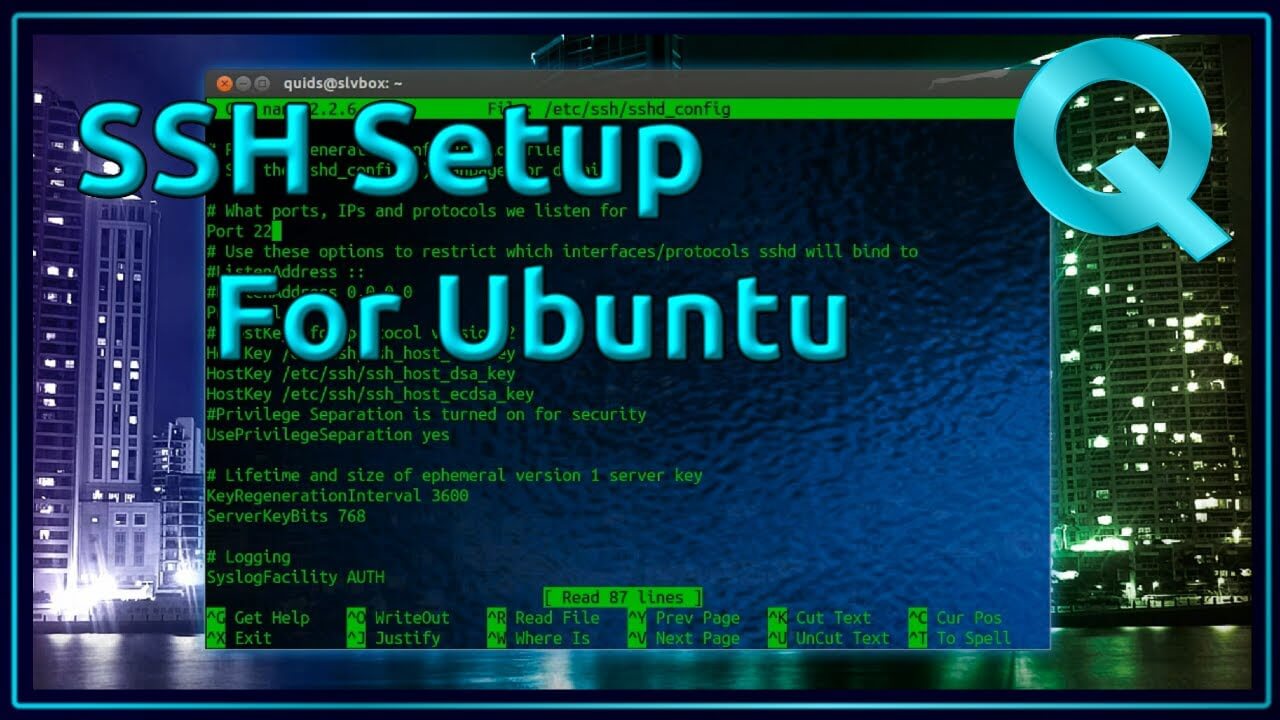
How To Securely Connect Remote IoT Devices Using P2P SSH On Ubuntu

How To Securely Connect Remote IoT Devices Using P2P SSH On Ubuntu

Mastering Secure Connections A Comprehensive Guide To Remotely